# Associative Arrays
aka Hash Maps in java, dictionaries in python world, Objects in javascript and Maps in clojure
Python’s dictionaries are implemented as resizable hash tables. Compared to B-trees, this gives better performance for lookup (the most common operation by far) under most circumstances, and the implementation is simpler.
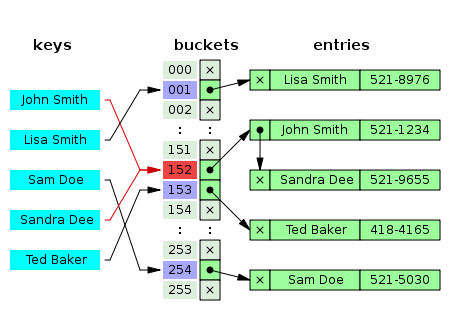
Dictionaries work by computing a hash code for each key stored in the dictionary using the
built-in hash() function. The hash code varies widely depending on the key; for example, “Python”
hashes to -539294296 while “python”, a string that differs by a single bit, hashes to 1142331976.
The hash code is then used to calculate a location in an internal array where the value will be stored.
Assuming that you’re storing keys that all have different hash values, this means that dictionaries
take constant time —
Hash function in python
But bear in mind the hash function is implemented for each kind of objects differently.
hash() calls __hash__() fn internally
Python lists are actually arrays — contiguous chunks of memory. The name "list" may be misleading to people who know about double-linked lists but are unfamiliar with Python. You can picture a Python list as a row of slots, where each slot can hold a Python object:
# Usecases
Sending large file from one computer to another?
- Send multiple times and check - naive approach
- Used to verify secure downloads from internet.
Hash Function
- Avalanch Effect
- MD5 is badly broken
- google search "md5 hash cracker"
# Security vurnabilities
Username - password data stores.
Prefer 3rd party like Google, Facebook to do it for you
Strategies:
- Naive approach, store password in plain text and match them on login
- Use secret key to encrypt and decrypt passwords.
- Broken using Rainbow Tables
- adobe database was hacked using this technique
- Hashing Algorithms
- Hashing and Salting